This post is also available in: Português
Although the article’s title references a security comparison between Google Workspace and the Microsoft 365 cloud solution, we don’t want to analyze them side by side or which is better or worse in security and data processing. Both Google Workspace and Microsoft 365 are secure because they are both enterprise-grade products.
We’ll look at a list of what actions and features Google and Microsoft have been taking to keep their customers’ data secure and, at the same time, their customers’ employees safe.
Areas
Cloud office applications are widely used, so we will address three main areas, which are:
Email security
Why? Email uses an open format and widely used in many businesses. Because of this, it is also often used to spread malware, spam, and phishing attacks. Intruders use this common gateway to get valuable company data.
As business email management services, Google has Gmail and Microsoft 365, Outlook. Let’s see what actions these two big companies are taking to protect their customers’ email accounts.
User login security
Why? Companies don’t hire Google Workspace or Microsoft 365 to send and receive email messages only. In some cases, employees don’t need access to professional email accounts. But they often use other standalone applications, such as Google Sheets and Microsoft Excel.
These users need to log in to the platform. Let’s look at what security practices Google and Microsoft have been taking to protect users’ logins.
Sensitive information and data security
Why? A company needs to protect its intellectual capital and customer information. What means to protect sensitive data, Google and Microsoft have been taking, what information do they collect for their analysis? This survey is not about the physical security of Google or Microsoft data centers.
But, before we start, let’s get to know a little about them.
Google Workspace and Microsoft 365, briefly

Microsoft 365 (formerly known as Office 365) has Outlook, Word, Excel, PowerPoint, OneNote, and OneDrive as options for online office apps.
Google Workspace (formerly G Suite) has Gmail, Calendar, Meet, Chat, Drive, Docs, Sheets, Slides as a suite option for office productivity apps.
Sounds like a good description, right? Now, let’s get down to business.
Security in Google Workspace

As an administrator, Google Workspace allows you to set custom rules to protect incoming emails against phishing and harmful software (malware), including protection against unusual attachment types.
You can enable spoofing protection for private or all groups. This kind of attack is when the hacker tries to impersonate someone he isn’t, such as a domain or employee.
The interesting part about Google Workspace is that the setup steps are simple, and it is up to the administrator.
Admin Console > Menu> Applications> G Suite> Gmail> Security
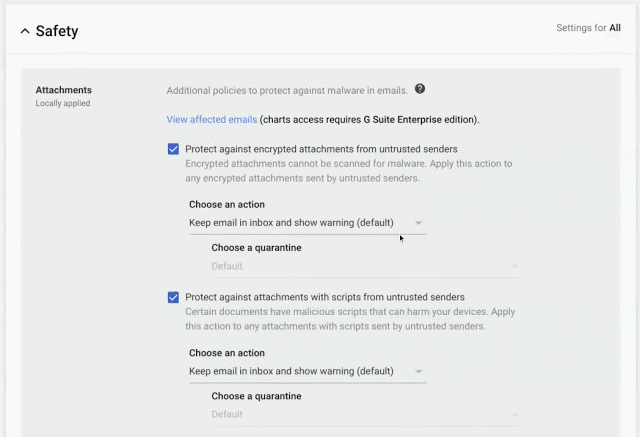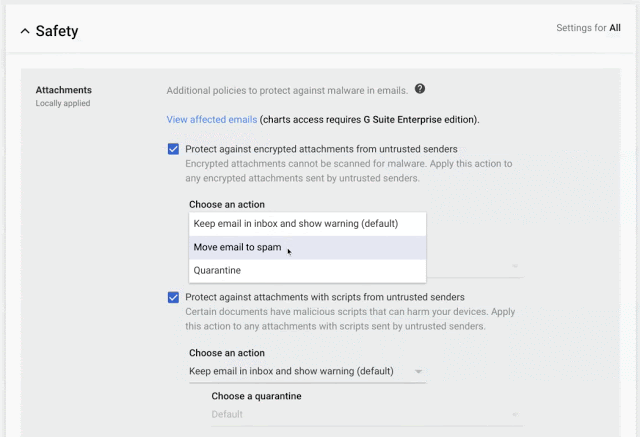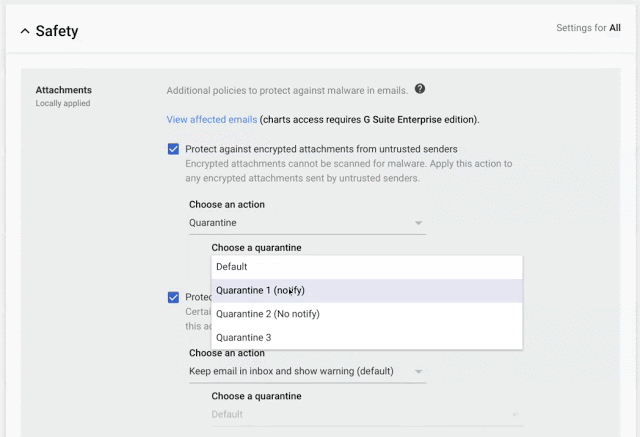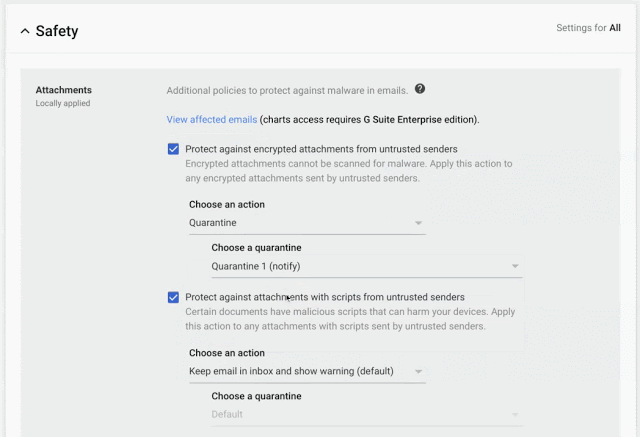
To protect email messages, Gmail uses industry-standard techniques. Enabling IT administrators to define custom rules that require email messages to be signed and encrypted using Secure/Multipurpose Internet Mail Extensions (S/MIME).
- S/MIME encryption available on the Enterprise plan;
There is the Advanced Protection Program that provides stronger protection for users at risk of targeted attacks. The Advanced Protection Program applies a specific set of policies for enrolled users, including security key enforcement, blocking access to untrusted applications, and enhanced scanning for email threats.
User login security in Google Workspace
Now addressing user authentication security, let’s take a look at Google’s main methods.
Starting with the fundamental issues, it is offered a 2-factor authentication option (two factors and applies it to all of your users) and the detection of suspicious logins. Whenever a suspicious login is detected, the administrator is notified so that they can take measures to ensure the security of the user’s account.
Unified access through Single Sign-On (SSO) allows access to other enterprise applications in the cloud, such as logging in directly to Bybrand. The Google Identity and Access Management (IAM) service also allows administrators to help manage all user credentials.
- SAML-based single sign-on service (SSO);
- OAuth2-based single sign-on service (SSO);
- SSO with a third-party identity provider (IdP) (Okta, OneLogin, 1password);
However, protocols alone are not enough. Google Workspace provides administrators with the option of asking their users to register a strong password and that this password meets certain characters (for example, number of characters, password strength .).
And it goes beyond that, you can apply the settings to the mobile devices of your employees for professional purposes.

The administrator can protect your organization’s data by requiring the managed devices to have a screen lock or password.
You can customize access control based on specific attributes using granular access control for SAML applications, including user, geolocation, device security status, and IP address, thereby reducing the chances of unintended access to specific applications or the information inside them.
Data security in Google Workspace
Now, let’s take a look at Google Workspace security controls that can help you manage data protection to meet the needs of your organization.
In the past, Google has suffered several criticisms related to its user data (advertising data machine); its collection is used for targeted ads. But this does not apply to corporate accounts; as of last year, Google has been improving its policies for handling user data in the corporate environment.
For IT administrators, one of their top priorities is keeping internal information secure and protected. With the Data Loss Prevention Policies (DLP), you can choose which types of data are sensitive and how to protect them.
The program allows easy detection of various common information types (such as credit card numbers in emails). You can configure policy-based actions and prevent users from sharing Google emails or Drive files if sensitive content is detected.
A powerful tool that helps administrators prevent abuse and malicious behavior is Google Vault. You can create retention rules and save documents such as email messages and Drive files. With Vault, you can control access and what actions are available in the app.
This ensures that only authorized users have access to your organization’s data.
Within the area of certifications, the Google Cloud Platform is ISO/IEC 27701 certified. A global standard designed to help organizations to get in accordance with international privacy frameworks and laws. It provides guidance for continuously implementing, maintaining, and improving security in data processors – important for organizations that following the GDPR.
Security in Microsoft 365

Microsoft 365 saw significant growth in its services, especially Microsoft Teams, during the year 2020. Communication tools such as Microsoft Teams and the web version of Outlook are essential to keeping businesses running. But these tools are not immune to safety and regulatory compliance risks.
For security in emails, Outlook has advanced protection for attachments or links in incoming messages, the service uses techniques to detect viruses and malware. And, if something is found, it will be removed so that you do not accidentally open it. For suspicious links in messages, if you click one, you are redirected to a warning page.
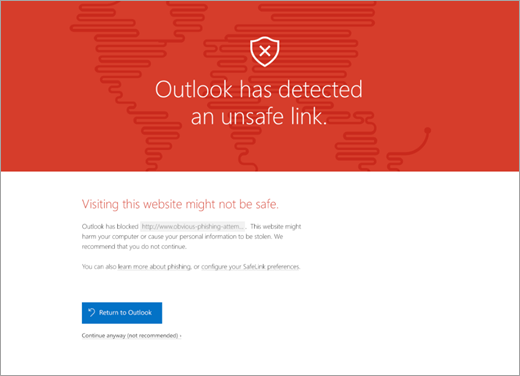
As email usage grew, the number of abusers also followed the same path. Microsoft Defender (formerly known as Microsoft Threat Protection) uses artificial intelligence to reduce spam and fraudulent emails (phishing) on the platform. You can also use the built-in reporting options directly in the Outlook mailbox to send false positives (good emails marked as spam), false negatives (incorrect emails), and phishing messages.
Mailboxes can become repositories for large amounts of potentially sensitive information such as financial data, legal contracts, or patient health information.
With the encryption of email messages, Microsoft 365 uses Office Message Encryption (OME), where your organization can send and receive encrypted email messages between people inside or outside your organization, regardless of the destination email address.
The service offers two more encryption options to help you meet email security needs.
- Secure/Multifunction Internet Mail Extensions (S/MIME);
- Information Rights Management (IRM).
User login security in Microsoft 365
Now let’s take a look at the key methods that Microsoft 365 uses for user authentication security.
Microsoft 365 uses the Azure Active Directory (Azure AD) solutions for identity management. Users can log on to applications (SSO) and, this way, it adds security and convenience. Single sign-on provides a breakthrough in how users sign in and use Microsoft 365 apps and software as a service (SaaS) partners.
It is not clear, but this option seems to be available only for Microsoft 365 Enterprise.
The advantage of Single Sign-On is that you can use the same account to enter the restricted area of other web applications. With just one authentication login, your job of running tasks on other software outside of the Microsoft ecosystem becomes more efficient and secure.
Some popular examples of web applications include:

- Wrike (project management);
- Salesforce;
- SurveyMonkey;
Microsoft 365 implements a multi-factor authentication (MFA). With two-step verification, administrators can reduce the risk of unauthorized access by asking users for additional proof of identity when signing in.
An example: you first specify your password, and when prompted, you also enter a dynamically generated verification code. Setup can be done in two ways: one is the standard method, using the free Microsoft Authenticator app on your mobile device.
The other way is to use SMS messages sent to your phone.
Backup methods: In situations where you do not have the phone or device you have set up as your preferred verification method with you, you can set up backup methods for your account. Generating unique codes that you keep in a safe place.
Data security in Microsoft 365
For sensitive or important data (social security numbers or health records), Microsoft 365 has the Sensitivity Labels solution, which allows you to classify and protect your organization’s data while ensuring that user productivity and ability to collaborate are not impaired.
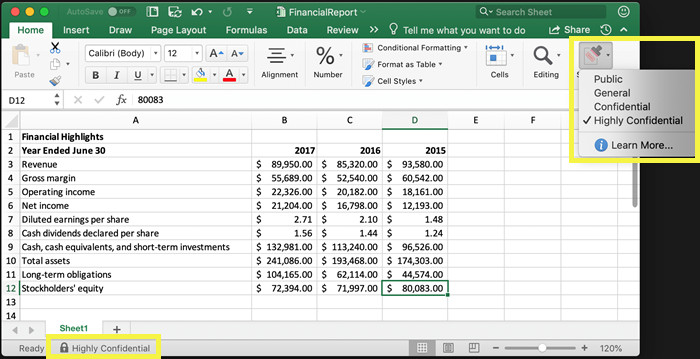
The tool is useful when content no longer falls behind a firewall or is exchanged between applications and services outside the control of the organization. Very common for documents and emails.
Administrators and their organizations must protect sensitive information in multiple locations, comply with industry regulatory standards, and avoid unintentional disclosure. With the Data Loss Prevention Policy (DLP) solution in the Office 365 Security & Compliance Center, you can automatically identify, monitor, and protect your users’ sensitive information.
You can use DLP to help detect the presence of information subject to the Health Insurance Portability and Accountability Act (HIPAA) in OneDrive for Business files by finding any document that contains sensitive information that is shared with people outside your company, and thus blocking access to that file (requiring extra actions).
Within the certifications, Microsoft has been working on building the most secure online collaboration solutions for its enterprise customers. Receiving an ISO/IEC 27001 certification shows its commitment to keeping promises from a business and security compliance point of view.
- In detail, all certifications obtained by Microsoft;
- Comparative: Google Workspace, Microsoft 365 or Zoho Workplace;
- Market share: Google Workspace, Microsoft 365, and Zoho;
Employee education
Additional security and certifications are a great benefit. But it would help if you did not leave the responsibility of protection only at the hands of third parties or programs.
CEO, CTOs, and IT administrators who are often at the forefront of data protection should also create strict policies for their employees.
- Ask employees to use strong passwords and demand frequent password changes. This helps ensure that even if a password is compromised, its use can be limited.
- Make sure that webmail applications use encryption. This is a standard but critical functionality to prevent emails from being intercepted by malicious agents.
- Use a password manager for the team (LastPass, Dashlane);
- Restrict access to services via public Wi-Fi networks.
In addition to implementing policies and procedures that promote security, companies can encourage their employees to follow best practices to ensure enterprise-wide security.
Create your first email signature with Bybrand
Bybrand offers the ability to generate, administer, and distribute essential email signatures for your employees.